You’ve probably heard by now that UVM has been subject to a computer system intrusion that has the potential to result in the malicious use of UVM NetIDs and passwords. Here’s the crux of the announcement:
The University has no indication that personally identifiable information has been accessed or compromised. Nonetheless, the University is taking the proactive step of requiring that ALL passwords be changed immediately and no later than 4:30 PM on Thursday, May 24. Accounts with passwords that have not been changed by this time will receive an additional notification, will have their passwords expired, and a change will be required before the account can be used again.
Ongoing monitoring of the University’s computer systems resulted in early detection of this system intrusion, which improved our ability to implement protection and mitigation strategies. The University continues to work with law enforcement and information security experts to investigate and address the intrusion. Users are asked to be extra vigilant with their computer use and report any suspicious activity to abuse@uvm.edu.
For more information you can read the full announcement and an up-to-date FAQ.
While no one likes maintaining passwords, they remain an important part of the security infrastructure at UVM and our peer institutions. We’ve recently implemented Multifactor Authentication for access to our most sensitive services, such as PeopleSoft, VPN (Virtual Private Network), and Virtual Desktop Infrastructure, and we may protect more systems with MFA in the future. Even with MFA in place and our strong password standards, you can help protect yourself and the University by following these guidelines:
- The longer the password, the more difficult it will be to crack. UVM NetID passwords are required to be at least 12 characters long, but longer is better. You can use even use a phrase, or a string of random words, e.g. ‘owls are my favorite flying Things.’, or ‘house caterpillar verify peanut’.
- The more character sets used, the more secure the password. Different character sets include:
- upper case letters (A B C D)
- lower case letters (a b c d)
- numbers (1 2 3 4)
- punctuation or other symbols (! @ # $)
UVM NetID passwords require at least two different character sets, but more is better.
- The more complex a password is, the more difficult to guess. Complex passwords are:
- not based on single words found in the dictionary, in any language
- not words spelled backwards, common misspellings or abbreviations
- not sequences (12345678) or repeated characters (22222222)
- not common mathematic sequences and series like Fibonacci numbers, Pi, or prime numbers
- not keyboard layout sequences (QWERTYPOIU, qazwsxedc or similar)
- not dates like birthdays or anniversaries
- not personal information like names of friends, relatives, pets or children
- not another unique identifier like your Social Security Number, student ID number, bank PIN, driver’s license number or passport number
An ideal password is one that is easy for you to remember, impossible for a human to guess, and more difficult for a computer to crack. While UVM stores passwords in a strongly encrypted form, attackers could potentially leverage the computational power of botnets and modern supercomputers to crack weaker passwords with relative ease.
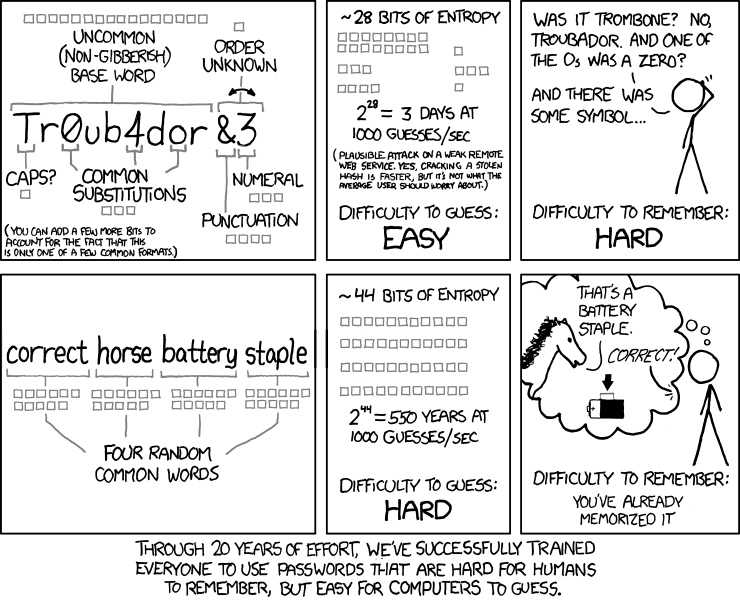
Using a string of random words is a great alternative to remembering a string of gibberish (or choosing a weak password):
Image: xkcd—a webcomic of romance, sarcasm, math, and language (Creative Commons BY-NC 2.5)
A few other tips:
- Use a password keeper. You’ll only need to remember your master password, and most password keepers can generate strong passwords for you that you won’t need to remember. Many password keepers integrate with your web browser so you don’t even need to type the passwords to use them. Among the password keepers used by IT staff at UVM are LastPass, Dashlane, KeePass, and 1Password. While we don’t support or endorse a specific password keeper at this point, they represent a mature technology that is reliable, secure, and convenient.
- Don’t use your UVM password anywhere else. This is the main reason we require annual password changes- if another password database has been breached (such as those at Yahoo!, eBay, and Adobe) and users have used the same password there that they do at UVM, eventually the attackers will discover that they have working UVM credentials.
- No passwords on sticky notes! (No, really. It’s 2018.)
- Take steps to protect yourself from malware and phishing scams. Keylogger malware, which captures your keystrokes and passes them along to malicious actors, is a common source of compromised credentials. Keep your antivirus software up to date and don’t visit any dubious websites. Be sure to check the URL bar of your browser any time you’re entering your UVM credentials into a website (even if it looks familiar); make sure you’re always at uvm.edu/.